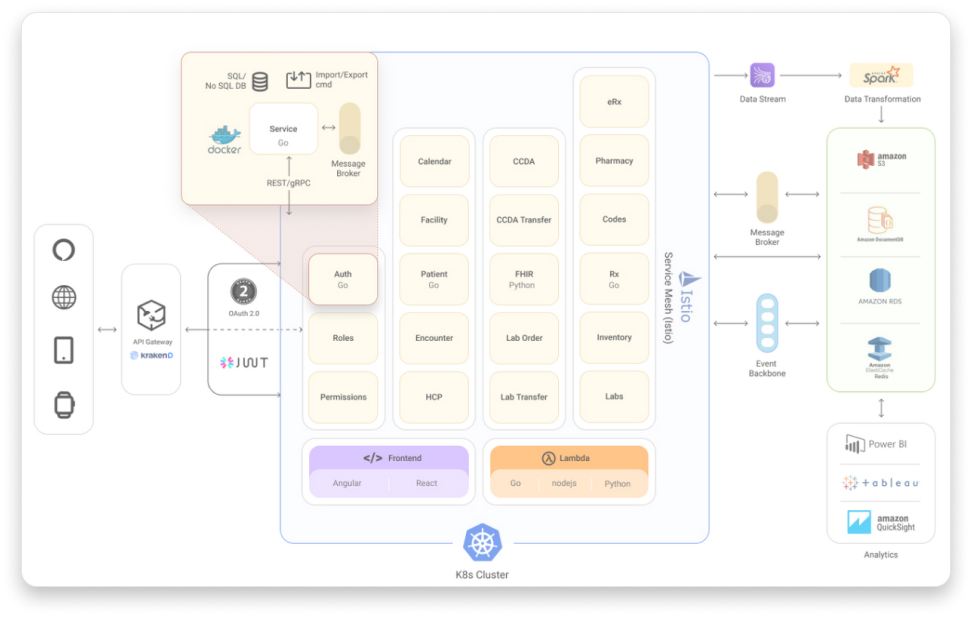
Encryption at rest and in transit
All data within the system is encrypted both in transit and at rest. For in-transit encryption, TLS secure all the traffic, while CA certificates handles the encryption process. At rest, data is protected using the AES-256 algorithm. Certain data that could reveal a user’s identity is stored in an encrypted format to prevent database administrators from viewing sensitive details; however, this information can be decrypted by the application when required. Additionally, some user data, such as passwords, are encrypted in a way that prevents even the application from decrypting it.
Sensitive information, such as database credentials and third-party account details, is are securely stored in a secrets manager service. These secrets are rotated periodically to ensure continued security.
Access control
Users are granted access based on role-based access control (RBAC), with permissions assigned according to their specific roles. This ensures that only authorized persons have access to sensitive data. Multi-factor-authentication (MFA) is implemented to add an extra layer of security to prevent unauthorized access even if someone compromises the password
Data masking and tokenization
Data at rest is encrypted to ensure compliance with data protection regulations, with additional encryption applied at the encryption layer for enhanced security. Sensitive information, such as Personally Identifiable Information (PII) and Personal Health Information (PHI), is either masked or removed from system logs and audit logs to prevent unauthorized access.
User passwords and secrets are securely encrypted and anonymized, making it impossible to reverse-engineer them. PII is typically masked within the application to protect user- privacy.
PII and PHI cannot be accessed by database administrators as they are encrypted using AES-256 and stored in the db.